Rising costs continue to push the retail and catalog markets to look for efficiencies; it’s a matter of survival. But don’t let your fraud prevention program fall victim to cost control. Aside from the obvious—identifying fraud, avoiding chargebacks from fraud, and potential lost “good” customers—your fraud prevention program can actually become an enabler of sales.

Why reliance on binary conditions is a slippery slope
Traditionally, there has been a tendency to over-rely on single-factor, binary conditions for verification or non-verification of a customer. There is a lot of research and a broad range of data on these topics, and while there are some factors that do offer value, it can be dangerous to apply such rules with a broad brush.
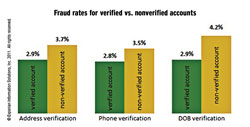
For example, Experian recently conducted a relevant study. The results appear to the right. This was a specific data set, designed to look at equally proportionate legitimate accounts and successful fraud, to determine what the fraud rate would look like across different verification factors.
What we found was that the fraud rates didn’t vary significantly for verified and nonverified accounts. Once we pivoted the data to shift the view from fraud rates to verification rates, we were able to determine some other interesting insights.
Address verification: “Fraud” accounts yielded only a 5.9% lower address verification rate than “legitimate” accounts.
Phone verification: “Fraud” accounts yielded only a 2.4% lower phone number verification rate than “legitimate” accounts.
The most promising single factor from the study appeared to be date-of-birth. Since then, we have performed other analyses on different data sets, and date-of-birth still provides quite a bit of insight. In a recent review of approximately 2.8 million records, we determined that when date-of-birth isn’t verified (but verification was tried), the transaction is almost four times as likely to be fraudulent.
The caveat, though, and this is really the problem with using single binary conditions for verification, is that to capture the fraudulent transactions, it is necessary to trap too many good orders, and if you let as many of the good orders through as will verify, too many of the frauds will pass and become “successful frauds.”
Our conclusion: While basic identity element verification checks, such as name, address, phone number, etc., are important—when viewed in isolation they are not nearly as effective in predicting actual fraud risk. In other words, the presence of positive verification elements doesn’t provide sufficient predictive value in determining fraud risk.
The rewards of a risk-based approach
The ever-changing nature of fraud practices warrants a risk-based and flexible approach to combating it. A risk-based approach allows companies to focus on those areas of operations that pose the greatest danger to themselves and their customers. A true risk-based approach will target the operational areas most likely to appeal to fraudsters and identity thieves and apply the most effective controls for the institution’s unique situation.
Multichannel retailers with a broad presence in ecommerce and mobile commerce can adapt their risk-based approach to the specific customer activity, so behaviors are treated consistently regardless of channel. Since this risk-based approach works no matter what size an organization is, the point is to identify risk and create a treatment for it.
Using a risk-based approach simply means applying a holistic assessment of a behavior and transaction with the end goal of applying proportionate authentication and decisioning. This approach allows for a balance of business drivers and the often opposing forces associated with them. Things like positive authentication (pass) rates, fraud risk mitigation, cost allocation and control, resource constraints and user experience.
A robust risk-based approach encompasses four main elements:
• Broad-reaching and accurately reported data sources
• Targeted analytics
• Detailed summary-level customer authentication results
• Flexibly defined decisioning strategies
Out-of-wallet questions, when appropriate
A risk-based fraud detection system allows companies to make customer relationship and transactional decisions based not on a handful of rules or conditions in isolation, but on a holistic view of a customer’s identity and predicted likelihood of associated fraud—and when there is a doubt, the customer can receive out-of-wallet questions to provide further identification. By using a sophisticated out-of-wallet tool, it’s possible to further separate fraudsters from good consumers, turning those questionable orders into shippable orders.
Closing the book on it
A risk-based system allows for an operationally efficient method of detection and reconciliation of high-risk conditions in tandem with identity theft mitigation. The inherent value of risk-based authentication can be summarized as delivering holistic assessment of a customer and/or transaction with the end goal of applying the right authentication and decisioning treatment at the right time. Realized values can include:
Reduced fraud exposure: Use of analytics and a more comprehensive view of a customer identity (the good and the bad), in combination with consistent decisioning over time, will outperform simple binary rules and more subjective decisioning from a fraud-detection perspective.
Improved customer experience: By applying the right authentication and decisioning treatment at the right time, customers are subjected to processes that are proportional to the risk associated with their activity. This means that lower risk customers are less likely to be put through a more arduous course of action, preserving a streamlined and often purely behind-the-scenes authentication process for the majority of customers and potential customers.
Operational efficiencies: With the implementation of a well-designed program, much of the decisioning can be done without human intervention and subjective human contemplation. Use of score-driven policies affords an institution the opportunity to use automated authentication processes for the majority of their applicants or account management cases. This translates into the requirement of fewer human resources, which usually means less cost. Conversely, it can mean the human resources an institution possesses are more appropriately focused on the applications or transactions that warrant such manual attention and treatment.
Measurable performance: It is critical to understand past and current performance of risk-based authentication policies to allow for the adjustment over time of such policies. These adjustments can be made based on, for example, evolving fraud risks, resource constraints, approval rate pressures or demands, and compliance requirements. It is for these reasons that it is recommended to do ongoing performance monitoring using authentication tools.
Monica Pearson is senior product manager, fraud and identity solutions, at Experian Decision Analytics.